There has been a flurry of interest in "Bible Codes." Many sensationalistic books have been published making extravagant claims;1 there have also been skeptical detractors with their erudite guffaws.2
Some truly provocative books have been published highlighting some amazing discoveries that would seem to validate the supernatural origin of the Biblical text,3 but very few have written from the standpoint of a cryptographic background.4
Are the so-called "Bible Codes" real? Or are they artifacts of random behavior within the normal characteristics of natural language? Are there really "hidden codes" behind the surface of the Biblical text?
The Science of Cryptology
People never cease to be fascinated by "secret writing," or secret codes. Ever since the earliest times, military, political, and personal messages have been communicated by various means to restrict their contents to those to whom the message is intended and to deny them to others.
From the ancient palaces of our earliest civilizations to the "black chambers" of our most modern command posts, the art of secret writing - and the science of their decipherment - has tumbled proud thrones and turned the tide of major wars.5
Cryptology - the study of secret codes and ciphers - has, of course, been stimulated by its use in literature. Edgar Allen Poe's The Gold Bug probably remains unequaled as a work of fiction, his tale turning upon a secret coded message.6
Sir Arthur Conan Doyle's Sherlock Holmes encounters ciphers three times in his uniquely distinguished career, demonstrating his thorough knowledge of the subject in The Adventure of the Dancing Men, where he recognizes little stick figures as cipher symbols.7 Jules Verne heightened the excitement of three of his novels with the mysteries of secret writing.8
The amazing ability to break a seemingly unintelligible cipher has always appeared mystical to the uninitiated. It undoubtedly was a major source of power to the priesthoods of the ancient empires.
It was not surprising that the famed American coup over the Japanese naval codes in World War II was called "MAGIC."9
The art of encryption has its roots in manipulations of the Biblical text-including the Kabbalah of Jewish mysticism. It was these techniques which led to cipher wheels and mechanical aids, which ultimately led to the computer.
It seems fitting that it is now the computer which appears to be opening up secrets hidden within the Biblical text since its inception.
Encryptions in the Bible
It comes as a surprise to many Bible scholars that there are a number of classic encryptions within the Biblical text. Hebrew tradition lists three different transformations in the Old Testament.
One of these, known as albam, employs a substitution system in which the Hebrew alphabet is split into two halves and equates the two halves. Thus, the first letter of the first half, aleph, substitutes for the first letter of the second half, lamed, and vice versa. The second letter of the first half, beth, substitutes for the second letter of the second half, mem, and vice versa, and so on. The term albam derives from the first four letters of this arrangement; aleph-lamed & beth-mem.
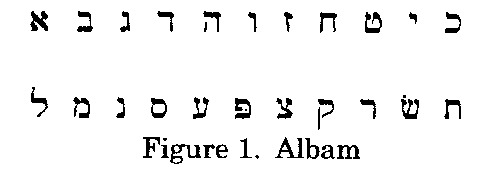
In Isaiah Chapter 7, we encounter the scheming of Rezin, the king of Syria, and Pekah, the son of Remaliah, king of Israel, who were confederating against King Ahaz of Judah.
Regarding verse 6, the Midrash notes that Tabeal, טבאל is encrypted using the method of albam, resulting in the name, רמלי, Remala (for Remaliah).10
(Remember, Hebrew reads from right to left.)
The plan of the conspirators in Isaiah 7 was apparently to establish the son of Tabeal as the king should their plot have succeeded.11
Another alternative encryption form found in the Old Testament is atbash, in which the alphabet is folded back over itself, with the second half reversed, as in figure 2.

The label atbash derives from the very procedure it denotes, since it is composed of aleph, tau, beth, and shin-the first, last, second, and next-to-last letters of the Hebrew alphabet.
In Jeremiah 25:26 and in Jeremiah 51:41, we encounter the name Sheshach. The context implies that this is somehow related to Babylon, and some commentators assume it was a suburb, or the equivalent.
However, it appears that Sheshach, ששך, is simply Babel, בבל, encrypted using the method of Atbash.12
Confirmation that Sheshach is really a substitute for Babel and not an entirely separate place name also comes from the Septuagint and the Targums.
In Jeremiah 51:1, we also find לב קמי, leb kamai, "heart of my enemy," is substituted for כשדים, Kashdim, "Chaldeans."
Hebrew literature records a third form of letter substitution, called atbah. Like albam and atbash, its name derives from its system. It is based on the property that each Hebrew letter also has a numerical value. The first nine letters would be substituted so that their numerical value would add up to ten. The next ten letters were paired on a similar system, totaling to the Hebrew digital version of 100. What happens to the remaining letters is not clear. This rather confusing system is not used in the Bible, but there is at least one use in the Babylonian Talmud.13
To students of cryptography, the substitution ciphers in the Bible are all simply historical novelties. However, to one who recognizes the supernatural origins of the Biblical text, the presence of encrypted elements in the Holy Scriptures is extremely provocative, indeed.
In our next article we will explore some of the more significant "Bible Codes." In our forthcoming reviews we will focus primarily on those codes which you do not need a computer to figure out!
This series of articles is being excerpted from Chuck Missler's book, Cosmic Codes.
Notes:
- Michael Drosnin, The Bible Code, Simon and Schuster, NY, 1997.
- Ronald S. Hendel and Shlomo Sternberg, "The Bible Code-Cracked and Crumbling," Bible Review, Vol XIII, No. 4, August 1997; includes "The Secret Code Hoax," by Hendel, and "Snake Oil For Sale," by Sternberg. Hugh Ross, "Cracking the Codes," Facts & Faith, Vol 11, No. 3, 3rd Qtr 1997, Reasons to Believe, P.O. Box 5978, Pasadena, CA.
- Grant Jeffrey, The Handwriting of God, a sequel to his Signature of God, both published by Frontier Research, Toronto, Canada, 1997; also, Yakov Rambsel, His Name is Jesus, also published by the same publisher.
- A worthy exception is by Jeffrey Satinover, M.D., Cracking the Bible Codes, William Morrow & Company, New York, 1997.
- Much of this background is well covered in David Kahn's comprehensive history, The Codebreakers, Macmillan Company, NY, 1967.
- Poe's stories, employing an intellectual chain of logic to solve a central problem, resulted in their being regarded as the first detective stories. The Gold Bug remains a classic despite its being full of absurdities and errors: the survival of the parchment despite the decay of the timbers of the boat; the fact that the invisible ink-cobalt nitrate-would also be soluble in water; the intricate geometry between the skull sighted between the rift in the trees after 150 years of arboreal growth, etc. Still, it remains a classic.
- Holmes, having solved the cryptogram, composes a message out of the cipher symbols he has recovered that leads to the culprit's arrest. Holmes may have borrowed this scheme from Thomas Phelippes, who had in 1587 forged a cipher postscript to a letter of Mary, Queen of Scots, to learn the names of the intended murderers in the Babington plot against Elizabeth. Holmes' other encounters occur in The Gloria Scott, where the great detective discovers a secret message hidden within an open-code text as every third word; and in The Valley of Fear where he receives a numerical code message from an accomplice of his arch rival, Professor Moriarty.
- In Voyage to the Center of the Earth, Verne opens with a three-step cryptogram of runic letters.
- It is interesting that the very word Magic derives from the Persian Magi, and the first cryptanalyst who was appointed the head of the ancient priesthood. This will be explored in a subsequent article.
- Midrash Rabbah, Numbers 18:21.
- Some authorities regard Tabeal as a corruption or some form of contemptuous epithet and dispute this as albam. (Albam works for the first two letters; the third, lamed, retains its identity because it would otherwise be transformed into a silent aleph.)
- The kaf, k, is one of five letters with a modified form if it is the last letter in a word. The employment of unique "final forms" is a characteristic which yields parsing advantages when used in extraterrestrial communication. This and related characteristics will be addressed in subsequent articles.
- Seder Mo'ed, Sukkah, 52b. This example plays on the word "witness" and its atbah substitution "master" to make a moral point.






